Coding and cryptography - Study guides, Class notes & Summaries
Looking for the best study guides, study notes and summaries about Coding and cryptography? On this page you'll find 280 study documents about Coding and cryptography.
All 280 results
Sort by
-
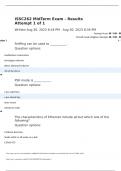
ISSC262 MidTerm Exam - Results Fall 2023.
- Exam (elaborations) • 8 pages • 2023
-
- $11.49
- 1x sold
- + learn more
ISSC262 MidTerm Exam - Results Attempt 1 of 1 Written Aug 30, 2023 8:18 PM - Aug 30, 2023 8:34 PM Attempt Score 88 / 100 - 88 % Overall Grade (Highest Attempt) 88 / 100 - 88 % stion 1 4 / 4 po Sniffing can be used to ___________. Question options: troubleshoot connections investigate malware detect abnormal behavior All of the above PSK mode is ___________. Question options: a pre-salted key a pre-shared key more secure enterprise ready The characteristics of Ethernet include a...

-
PCI ISA Exam Question And Answers 2022
- Exam (elaborations) • 9 pages • 2022
-
- $14.99
- 11x sold
- + learn more
For PCI DSS requirement 1, firewall and router rule sets need to be reviewed every _____________ months 6 months Non-console administrator access to any web-based management interfaces must be encrypted with technology such as......... HTTPS Requirements 2.2.2 and 2.2.3 cover the use of secure services, protocols and daemons. Which of the following is considered to be secure? SSH, TLS, IPSEC, VPN Which of the following is considered "Sensitive Authentication Data"? Car...
Coding and Cryptography notes.

-
Instructor test bank 2023 verified and updated.
- Exam (elaborations) • 232 pages • 2023
-
- $13.49
- 2x sold
- + learn more
Instructor test bank 2023 verified and updated. By TECHGRADES. 1-Advanced Engineering Electromagnetics by Constantine Balanis 2-Antenna Theory and Design, 2ed+1ed, by Warren Stutzman 3-Circuit Design with VHDL by Volnei A. Pedroni 4-Convex Optimization by Stephen Boyd and Lieven Vandenberghe 5-Digital signal processing 2+1ed, by Sanjit K. Mitra 6-Partial differential equations, lecture notes by Neta 7-Fundamental Methods of Mathematical Economics 4ed, by Alpha C. Chiang 8-C++ How ...

-
CSSLP Exam 2024 Questions & Answers | 100% Correct | Verified
- Exam (elaborations) • 82 pages • 2024
-
- $15.49
- + learn more
Your project involves streaming web conference content from your web servers to multiple endpoints. Because of the sensitive nature of the content, encryption is mandated. What would be the preferred algorithm? A. 3DES B. AES C. RC4 D. MD5 - Answer: C. RC4 is a stream-based cipher, and the web conference traffic requires a stream cipher for performance reasons. A, B, and D are incorrect. 3DES and AES are symmetric block ciphers, but are poor choices for streaming media channels. MD5 is...

-
PCI ISA Exam Questions and Answers with complete solution
- Exam (elaborations) • 12 pages • 2024
- Available in package deal
-
- $12.99
- + learn more
For PCI DSS requirement 1, firewall and router rule sets need to be reviewed every _____________ months - correct answer-6 months Non-console administrator access to any web-based management interfaces must be encrypted with technology such as......... - correct answer-HTTPS Requirements 2.2.2 and 2.2.3 cover the use of secure services, protocols and daemons. Which of the following is considered to be secure? - correct answer-SSH Which of the following is considered "Sensitive Authenti...

-
CYSE 411 midterm questions and answers latest 2023(UPDATED)
- Exam (elaborations) • 19 pages • 2024
- Available in package deal
-
- $14.99
- + learn more
CYSE 411 midterm questions and answers latest 2023(UPDATED)What are a bug and a flaw? - correct answer Bugs are implementation vulnerabilities (bad coding) Flaws are structural vulnerabilities What are the three pillars of Software Security? - correct answer Applied Risk Management Software Security Touchpoints Knowledge How do we calculate risk? - correct answer Risk = probability * impact ( T / F )The code in C Libraries has been certified to be internally secure - correct answer...
Coding and Cryptography notes
Coding and Cryptography notes

-
Secure Software Design Study Guide - C706 Questions With 100% Correct Answers.
- Exam (elaborations) • 16 pages • 2023
- Available in package deal
-
- $8.49
- + learn more
Confidentiality - Information is not made available or disclosed to unauthorized individuals, entities, or processes. Ensures unauthorized persons are not able to read private and sensitive data. It is achieved through cryptography. Integrity - Ensures unauthorized persons or channels are not able to modify the data. It is accomplished through the use of a message digest or digital signatures. Availability - The computing systems used to store and process information, the security controls ...

$6.50 for your textbook summary multiplied by 100 fellow students... Do the math: that's a lot of money! Don't be a thief of your own wallet and start uploading yours now. Discover all about earning on Stuvia





