Topqualityworka
I Provide High quality work at a low price. You may find other documents on the Internet or this website however they don't always cover all the BTEC Criteria. This is why my work has the best standards and COVERS ALL THE CRITERIA, i go into a lot of detail from pass to distinction tasks, so you can use it as a guide/ template. Each piece of works takes around 3-4 hours and I only ask for a small contribution of your money.
- 95
- 0
- 2
Community
- Followers
- Following
425 Reviews received
90 items

M3- Report on the business risks of insecure networks and how they can be minimised
Report on the business risks of insecure networks and how they can be minimized. Such as Business Risks Loss of service Increased Costs Loss of confidentiality Compromised data integrity Security issues Trojans Worms Spyware Adware Minimising the risks of these
- Package deal
- Essay
- • 6 pages •
Report on the business risks of insecure networks and how they can be minimized. Such as Business Risks Loss of service Increased Costs Loss of confidentiality Compromised data integrity Security issues Trojans Worms Spyware Adware Minimising the risks of these

D2- Evaluate typical services available from a network operating system directory service
Evaluate typical services available from a network operating system directory service. In this report I will be explaining the different directory services available for networks and there operating systems. I will go on to talk about the account management, authentication management, active directory and DNS. I will talk about the features of this and where they can be used in certain areas. I will then go on to talk about the advantages and disadvantages of each of these directory services and...
- Package deal
- Essay
- • 6 pages •
Evaluate typical services available from a network operating system directory service. In this report I will be explaining the different directory services available for networks and there operating systems. I will go on to talk about the account management, authentication management, active directory and DNS. I will talk about the features of this and where they can be used in certain areas. I will then go on to talk about the advantages and disadvantages of each of these directory services and...

M1- Compare the benefits and disadvantages of peer-to-peer network and client/server networks
Learners should compare the benefits and disadvantages of peer-to-peer and client-server networks. Ideally, have the chance to see the operation of both types of networks and then the actual evidence presented as a verbal, written report etc. would be based on real experience.
- Package deal
- Essay
- • 4 pages •
Learners should compare the benefits and disadvantages of peer-to-peer and client-server networks. Ideally, have the chance to see the operation of both types of networks and then the actual evidence presented as a verbal, written report etc. would be based on real experience.

M2- Explain the networked solution to meet a particular situation with specific requirements
Design a networked solution to meet a particular situation with specific requirements M2 is the design of a network solution. Evidence could be diagrammatic with explanatory notes. The head office requires 5 networked PCs for their admin staff. The admin team is situated on the ground floor. You need to link the management computers and laptops to the same network so that they can share the internet connection and upload and share documents with the admin team. Management are based on the first ...
- Package deal
- Essay
- • 5 pages •
Design a networked solution to meet a particular situation with specific requirements M2 is the design of a network solution. Evidence could be diagrammatic with explanatory notes. The head office requires 5 networked PCs for their admin staff. The admin team is situated on the ground floor. You need to link the management computers and laptops to the same network so that they can share the internet connection and upload and share documents with the admin team. Management are based on the first ...
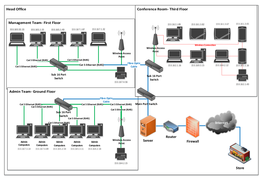
M2- Design a networked solution to meet a particular situation with specific requirements
Design a networked solution to meet a particular situation with specific requirements M2 is the design of a network solution. Evidence could be diagrammatic with explanatory notes. The head office requires 5 networked PCs for their admin staff. The admin team is situated on the ground floor. You need to link the management computers and laptops to the same network so that they can share the internet connection and upload and share documents with the admin team. Management are based on the first ...
- Package deal
- Visual
- • 1 pages •
Design a networked solution to meet a particular situation with specific requirements M2 is the design of a network solution. Evidence could be diagrammatic with explanatory notes. The head office requires 5 networked PCs for their admin staff. The admin team is situated on the ground floor. You need to link the management computers and laptops to the same network so that they can share the internet connection and upload and share documents with the admin team. Management are based on the first ...
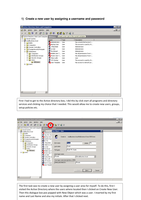
P6- Make a networked system secure.
1) Create a new user by assigning a username and password 2) Set authorization permissions for the user to access a shared drive or folder on the network 3) Grant the user with Read, Write and Execute access controls to the shared drive or folder 4) Set the shared drive or folder to be backed up Mon‐Fri at 5pm 5) Delete and then restore the folder from the last available back‐up 6) Encrypt the data stored in the shared drive or folder so that it remains secure 7) Ensure that the server is ke...
- Package deal
- Essay
- • 13 pages •
1) Create a new user by assigning a username and password 2) Set authorization permissions for the user to access a shared drive or folder on the network 3) Grant the user with Read, Write and Execute access controls to the shared drive or folder 4) Set the shared drive or folder to be backed up Mon‐Fri at 5pm 5) Delete and then restore the folder from the last available back‐up 6) Encrypt the data stored in the shared drive or folder so that it remains secure 7) Ensure that the server is ke...

P4- Explain the function of interconnection devices
Explain the key components required for client workstations to connect to a network and access network resources you are explaining the key components for connection to network systems.
- Package deal
- Essay
- • 5 pages •
Explain the key components required for client workstations to connect to a network and access network resources you are explaining the key components for connection to network systems.

P3- Explain the key components required for client workstations to connect to a network and access network resources
Compare the benefits and disadvantages of peer‐to‐peer network and client/server networks. Before attempting M1, you should, ideally, have the chance to see the operation of both types of networks and then the actual evidence presented as a verbal, written report etc. would be based on real experience.
- Package deal
- Essay
- • 8 pages •
Compare the benefits and disadvantages of peer‐to‐peer network and client/server networks. Before attempting M1, you should, ideally, have the chance to see the operation of both types of networks and then the actual evidence presented as a verbal, written report etc. would be based on real experience.

P5- Describe typical services provided by networks
Describe typical services provided by networks.
- Package deal
- Essay
- • 6 pages •
Describe typical services provided by networks.

P2- Describe why different network standards and protocols are necessary
Describe why different network standards and protocols are necessary; you should be able to demonstrate that you understand why different network standards and protocols are necessary. Examples given should be realistic.
- Package deal
- Essay
- • 6 pages •
Describe why different network standards and protocols are necessary; you should be able to demonstrate that you understand why different network standards and protocols are necessary. Examples given should be realistic.

P2- Explain how two contrasting businesses are influenced by stakeholders
P2- Explain how two contrasting businesses are influenced by stakeholders
P1- Explain the features of two contrasting businesses
P1- Explain the features of two contrasting businesses
P1- Explain the features of two contrasting businesses